Our news
INTERNET FRAUD, ANOTHER DANGER FOR SMEs.

It has always been believed that crackers, sometimes mistakenly called hackers, usually target large companies, but this couldn't be further from the truth. Small businesses and SMEs have always been in the crosshairs of cybercriminals because many of them don't place as much emphasis on the cybersecurity of their networks or equipment. This makes them easy targets for fraud, cyberattacks, identity theft, and data breaches.
A comparative study of Cisco Security Capabilities 2018 revealed that the 54% of all cyberattacks cause financial damages of more than $500,000, which include, among others, the loss of income, customers and opportunities, as well as increased expenses.
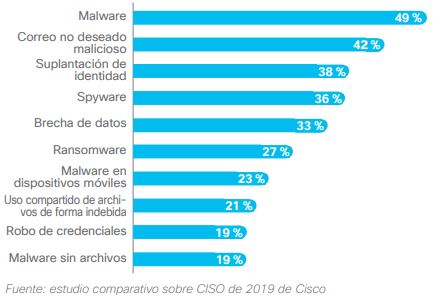
With this post, we hope to show the most common practices of these crackers and how we can avoid most of them. Below, we will list the most well-known types of online fraud.
CARDING
How many times have we seen an irresistible offer online? Well, sometimes those offers aren't what they seem, and there's a person with bad intentions behind them.
When we buy this product, we give our bank card to the product owner, giving them complete freedom to do whatever they want with it.
If we encounter someone who is misusing our card, It is very important that we deactivate it.
PISHING
This is one of the most common techniques used by cybercriminals. Imagine you receive an email from someone claiming to be a client of your company and asking for personal or banking information. At this point, you need to be extremely cautious, as you could be facing a scam. When you click on the link in the email, which usually leads to the client's website, you might see a legitimate corporate website that inspires confidence, but it's possible you're clicking on a malicious link.
Avoid this fraud, it is very important to check what Your email address has sent you the email, Since they sometimes have names that have little to do with the client or company, or contain an unofficial domain, which already makes us suspicious. It's also very common for the email to have many spelling mistakes or nonsensical words, as they are usually pre-written texts translated into several languages.
PHARMING
It is a variant of Phishing. Basically, it involves finding vulnerabilities in your company website to link to a fraudulent website; that is, when you are looking for a company's web address, clicking on it redirects you to a different website.
That's why it's so important to have your own constantly updated website.
MAIL SPOOFING
This is a very difficult technique to detect, since we are dealing with a case of identity theft. Email spoofing consists of a series of techniques used to impersonate another email user, which, unlike phishing, will not trigger any alarms since this time we will be using a real email account of the fraud victim.
There are many ways cybercriminals obtain our email addresses. For example, some programs create random usernames and passwords until they find a real account, or we may have accepted the terms of an illegal service that stole our personal information.
If you fall victim to this technique, the easiest way to detect it is to check your "sent messages" inbox and see if any emails that weren't sent to you have been sent. You might also receive emails that appear to have been sent by you. Hackers do this to pique the victim's curiosity, leading them to open the email and discover that it was spam or contained links to malware.
If we find that we are the sender of an email generated by an identity thief, the best way to verify whether it is real or not is to hire a spam and malware protection service that verifies the integrity of the email.
In Apen We are committed to protecting your email account, which is why we offer the Office 365 service, which provides a professional email account with 50 GB of storage, a customizable domain, backup of your email, calendar and contacts, and protection against spam and malware.

